CVE-2024-12106 WhatsUpGold Pre-Auth
Security research on WhatsUpGold LDAP authentication vulnerability enabling pre-authentication exploitation and credential theft.
CVE-2024-12106 — Pre-Auth Evil LDAP and Password Theft
Affected Versions: 23.1.1 to 24.01 Build 2177
WhatsUpGold is a network monitoring tool developed by Progress. This article continues the WhatsUpGold Unauth Series.
CVE.ORG Reference
Authentication Mechanism
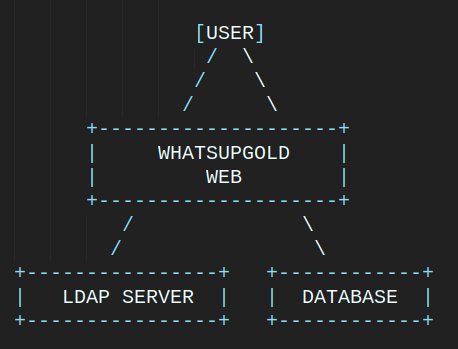
WhatsUpGold supports multiple authentication mechanisms, including OpenIdConnect, LDAP, and Active Directory.
When a login attempt is initiated, the backend verifies whether the user is a local account (database) or an LDAP/Active Directory account.
If the GlobalSettings table in the database contains an ldap field, the system queries the specified LDAP server. If the user is not found there, it falls back to checking the database.
Route
WhatsUpGold contains multiple controllers, with most functionality being routed through the /api/core/ controller.
The core API controller enforces session validation. However, through the WUG plugin and its controllers, the LDAP functionality can be managed in a pre-authentication context.
LoginAjax
The login process begins with the LoginAjax action, which then calls the ValidateUser method.
If the submitted username in the POST request contains an @ character, the request is prioritized and redirected to Active Directory authentication.
public ActionResult LoginAjax(string username, string password, bool rememberMe)
{
bool flag = true;
bool flag2 = false;
string text = string.Empty;
LogInViewModel logInViewModel = new LogInViewModel
{
Password = password,
RememberMe = rememberMe,
UserName = username
};
if (flag)
{
flag2 = this.loginModel.ValidateUser(logInViewModel);
if (flag2)
{
FormsAuthentication.SetAuthCookie(logInViewModel.UserName, logInViewModel.RememberMe);
this.userActivityLogger.Log(logInViewModel.UserName, "Authentication", "The user has logged in.");
this.SessionKeepAlive(logInViewModel.UserName);
}
else
{
if (logInViewModel.ActiveSessionMessage.Contains("Cisco ACS Authentication Failed"))
{
this.userActivityLogger.Log(logInViewModel.UserName, "Authentication", logInViewModel.ActiveSessionMessage);
logInViewModel.ActiveSessionMessage = "Failure at authenticating server.";
}
text = logInViewModel.ActiveSessionMessage ?? this.lcl.Lookup("The user name or password provided is incorrect.");
}
}
else
{
text = this.lcl.Lookup("Your license is invalid.");
}
return base.Json(new
{
authenticated = flag2,
message = text,
username = logInViewModel.UserName
}, JsonRequestBehavior.AllowGet);
}Trace
+-- NmUserAuthenticator.Utilities.RegisterLdapAppServices(IUnityContainer) : void
+-- NmUserAuthenticator.Utilities.RegisterServices(IUnityContainer) : void
+-- NmUserAuthenticator.WugUserAuthenticationGateway.WugUserAuthenticationGateway(IUnityContainer, IUserAuthenticator) : void
+-- NmUserAuthenticator.WugUserAuthenticationGateway.WugUserAuthenticationGateway(IUnityContainer) : void
+-- NmUserAuthenticator.WugUserAuthenticationGateway.WugUserAuthenticationGateway() : void
+-- Wug.UIServices.UserService.ValidateUser(ref string, string, out string) : boolLDAP Controller
The LdapController expects POST data containing parameters such as:
AdDomainAuthSchemeLdapDnPortServerUseTls
Behavior
- If
AuthScheme != ad-domain, the function directly returnsLdapDn.
If it is equal, the function appends%stoAdDomain, formatting asEVILDOMAIN\%s(where%sis the submitted username). - If
UseTls = true, the connection is made vialdaps://. Otherwise,ldap://. - An XML config is generated and stored in the database (
GlobalSettings.ldap).
XmlElement xmlElement = new XmlDocument().CreateElement(name);
xmlElement.SetAttribute("authorize-dn", this.AuthDn());
xmlElement.SetAttribute("port", this.Port.ToString());
xmlElement.SetAttribute("secured", this.UseTls ? "1" : "0");
xmlElement.SetAttribute("server", this.Server);
xmlElement.SetAttribute("uri", this.FormUri());
xmlElement.SetAttribute("use-ad", (this.AuthScheme == "ad-domain") ? "1" : "0");
return xmlElement.OuterXml;Conclusion
CVE-2024-12106 demonstrates how improper LDAP configuration handling in WhatsUpGold can be leveraged for pre-authentication exploitation and potential credential theft.
Administrators should apply the latest patches provided by Progress and review their LDAP configurations immediately.
Stay Protected
Security vulnerabilities are discovered constantly. HawkTrace helps organizations stay ahead of threats through comprehensive security assessments, APT simulations, and continuous threat hunting.
Need expert security consultation? Contact us or explore more research.